It Security
Authentication, authorization, and accounting.

It security. The Splunk platform is used by many to perform security. It aims to reduce the risk of cyber attacks and protect against the unauthorised exploitation of systems, networks and technologies. 30 Oct 18:30 | 1.
212-241-4357 The Icahn School of Medicine at Mount Sinai:. Security Marriott fined £0.05 for each of the 339 million hotel guests whose data crooks were stealing for four years. Learn about the IT security services available at K-State, including encryption software, VPN, media sanitization, and data security.
Learn where you can read the UW’s information security and privacy policies, the laws and regulations that impact these policies, and where to read a confidential data risk guide. This includes physical data (e.g., paper, computers) as well as electronic information. How to Securely Protest in a Pandemic.
Displayed here are Job Ads that match your query. Not so long ago IT security was a checkpoint at the end of a development cycle. Enterprise Security Services (ESS) Line of Business (Lob) Program Overview.
The IT Security Office (ITSO) provides strategic and tactical planning for a security framework applied to both the campus and OIT environment. IT security maintains the integrity and confidentiality of sensitive information while blocking access to hackers. The USF IT Security Plan supplement s the Official Security Policies, Standards, and Procedures that have been established for the USF System.
IT security is the protection of computer systems from theft of or damage to their hardware, software or electronic data, as well as from disruption or misdi. Security The Russians are at it again:. IT Security provides the following services to the UCSF enterprise:.
IT is broader in nature and focuses on protecting all of an entity’s data — whether that data be in electronic or a more physical form. Information security, sometimes abbreviated to infosec, is a set of practices intended to keep data secure from unauthorized access or alterations, both when it's. 212-241-7091 Mount Sinai Beth Israel, Mount Sinai Brooklyn, Mount Sinai St.
See our overview of security and privacy policies. Indeed may be compensated by these employers, helping keep Indeed free for jobseekers. Although closely related, IT security differs slightly from cybersecurity.
Luke’s and Mount Sinai West:. The successful breach of Donald Trump’s official website shows up lax security on his campaign. Zebrocy backdoor malware is evolving, Uncle Sam warns close to eve of presidential election.
KPI Library | IT Security. In this category, individuals focus on data backups, as well as monitoring techniques to make sure that no one has tampered with data or exfiltrated information. Focuses on keeping all data and derived information safe.
Computer security, cybersecurity or information technology security ( IT security) is the protection of computer systems and networks from the theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide. This is exactly what Happiest Minds offers with advanced IT security services. We’ll give you some background of encryption algorithms and how they’re used to safeguard data.
On a daily basis, hackers try to steal business-critical data or digital identities and manipulate connected production facilities. We provide end-to-end cyber security. We offer cybersecurity products and services that you can customize to help your agency enhance security, improve resilience, protect important information, and bring systems up to date.
This course covers a wide variety of IT security concepts, tools, and best practices. This prevents unauthorised access, misuse, destruction or disruption of data. HHS’ enterprise-wide information security and privacy program was launched in fiscal year 03, to help protect HHS against potential information technology (IT) threats and vulnerabilities.
We have access to breaking news, and report every day with transparency and integrity. A security event refers to an occurrence during which. As a graduate of Drexel University with degrees in Management Information Systems and International Business, Alex has a strong background in IT.
Overview – Qualys IT, Security and Compliance apps are natively integrated, each sharing the same scan data for a single source of truth. This defense includes detection, prevention and response to threats through the use of security policies, software tools and IT services. An effective IS program takes a holistic view of an organization’s security needs, and implements the proper physical, technical, and administrative controls to meet those.
Certified Information Security Manager (CISM) Leapfrogging from the eight-place position last year to the third spot in is the Certified Information Security Manager (CISM) cert. The Mount Sinai Hospital and Mount Sinai Queens:. Get the latest security news from eWEEK, uncovering critical threats to information security as well as the products, technologies, and techniques to prevent breaches.
Then, we’ll dive into the three As of information security:. Configure your antivirus to automatically scan all downloaded files, removable media, and email attachments. Security WIRED25 Q&A:.
Incident Response (IR), Digital Forensics Incident Response (DFIR), Architecture consulting, Policy Management, Risk Management & Compliance, Security Awareness and Outreach, Vulnerability Management, Endpoint Security (including Endpoint Detection & Response, AntiVirus, and Encryption), E-Discovery, and investigation assistance. Cyber security is one of the greatest challenges of our times. Security and privacy policies.
Security salaries in your area. Learning Tree's comprehensive cyber security training curriculum includes specialized IT security training and cyber security certification programs for all levels of your organization, including the C-suite. By understanding the latest threat trends, security teams can take measures to ensure that their security strategies, including the identification and tracking of new IOCs, are being correctly updated.
It introduces threats and attacks and the many ways they can show up. A security threat is a malicious act that aims to corrupt or steal data or disrupt an organization's systems or the entire organization. Torsten George - Incident Response.
Splunk is the darling of the IT Service Management (ITSM) market. KPI Library is a community for performance management professionals. Every IT security professional should learn the basics of cryptography, including.
An Information Technology (IT) Security Policy identifies the rules and procedures for all individuals accessing and using an organization's IT assets and resources. The rising, all-encompassing connectivity requires omnipresent security measures. With over years of experience in the IT security and Cybersecurity industry, we are at the front of global news.
Find the latest security analysis and insight from top IT security experts and leaders, made exclusively for security professionals and CISOs. Information Security (IS) is the practice of exercising due diligence and due care to protect the confidentiality, integrity, and availability of critical business assets. This security plan is intended to comply with the regulations and policies set down by the State of Florida, the University of South Florida, the.
Alex Rutkovitz is the co-founder and Vice President of Choice CyberSecurity, a Security and Compliance firm specializing in industry-leading risk assessments and ongoing proactive security services. Use KPI Library to search for Key Performance Indicators by process and industry, ask help or advice, and read articles written by independent experts. Takeaways From the Shopify Hack.
IT and security policy program management. Enterprises need effective cyber security solutions to monitor and provide real-time visibility on a myriad of business applications, systems, networks and databases. Establish a scalable, flexible system of governance to manage IT and security policies and ensure alignment with compliance obligations.
It's about establishing a set of security strategies that work together to help protect your digital data. IT security allows processes and procedures to be in place to ensure that all information is protected. The protection of information and information systems against unauthorized access or modification of information, whether in storage, processing, or.
The tool’s web-based interface correlates disparate IT data from many Quest security and compliance solutions into a single console and makes it easier than ever to:. But it has expanded from ITSM into security and operations management. Filter by location to see IT.
UCLA IT Security recommends that every member of the campus community download and use Sophos frequently. Security, in information technology (IT), is the defense of digital information and IT assets against internal and external, malicious and accidental threats. Yep, it's the artists occasionally known as APT28.
IT Security Search is a Google-like, IT search engine that enables IT administrators and security teams to quickly respond to security incidents and analyze event forensics. The primary purpose is to ensure that information remains of high integrity, confidential and accessible. IT security is an umbrella term that includes network, internet, endpoint, API, cloud, application, container security, and more.
Network security for printers. Learn security best practices, support IT security programs and policy with the NIST framework, or earn a CISSP, CompTIA Security+, CASP, or CEH certification!. IT Security Awareness and Training;.
The antivirus should always be active and configured to update on a regular basis. "Information Security is a multidisciplinary area of study and professional activity which is concerned with the development and implementation of security mechanisms of all available types (technical, organizational, human-oriented and legal) in order to keep information in all its locations (within and outside the organization's perimeter) and, consequently, information systems, where information is created, processed, stored, transmitted and destroyed, free from threats.Threats to. The national average salary for a IT Security is $76,410 in United States.
It security synonyms, It security pronunciation, It security translation, English dictionary definition of It security. Federal Information Security Management Act. Digital cryptography is the art of making information secure against unauthorized access and modification.
For example, IT security would encompass securing keypads that allow access to a room full of data files. Security bloggers help keep you up to date on how to protect your network through news, updates, advice, and opinions on how you can stay ahead of hackers. IT security October 28, 28 Oct' Trump supporters targeted by cryptocurrency scammers.
We provide daily IT Security News written by our team of in-house writers and editors. IT security is a cybersecurity strategy that prevents unauthorized access to organizational assets including computers, networks, and data. Play it safe with Telekom Security Cyberattacks present ever greater challenges to companies with growing digitalization.
Policies and procedures K-State has adopted a number of policies and procedures for IT security in order to address the growing threats to technology. Cyber security definition Cyber security is the application of technologies, processes and controls to protect systems, networks, programs, devices and data from cyber attacks. Subscription Options – Pricing depends on the number of apps, IP addresses, web apps and user licenses.
Our security operates at a global scale, analyzing 6.5 trillion signals a day to make our platform more adaptive, intelligent, and responsive to emerging threats. Archer IT & Security Policy Program Management enables you to document policies and standards, assign ownership and map policies to key business areas and objectives. Indeed ranks Job Ads based on a combination of employer bids and relevance, such as your search terms and other activity on Indeed.
Cyber security's comprehensive news site is now an online community for security professionals, outlining cyber threats and the technologies for defending against them. Matt Mitchell Ford Foundation Tech Fellow and Founder, CryptoHarlem and Avi Schiffmann, Founder, The Coronavirus Tracker in. Salary estimates are based on 4,595 salaries submitted anonymously to Glassdoor by IT Security employees.
Effective IT Security Policy is a model of the organization’s culture, in which rules and procedures are driven from its employees' approach to their information and work.

8 It Security Processes To Protect And Manage Company Data Process Street Checklist Workflow And Sop Software

It Security Management Tools Free Software Trial Solarwinds

Information Security Dasher S Hierarchy Of It Security Needs Dasher
It Security のギャラリー

Riskiq The Digital Threat Hunter Using Ai To Define The Future Of Cyber Security
1

What Project Managers Need To Know About Cyber Security

Macomb Community College It Network Security Professional Cybersecurity

Traditional It Security Vs Cloud Security Which Approach Is Right For Your Business Security Info Watch
Cyber Security Taxonomy

It Security Consulting Cyber Security Experts And Best Practices Sophos

Council Post 10 Cybersecurity Protocols Every Tech Professional Should Follow

It Security For Australia Businesses Get A Quote For Services

Cyber Security Specialist Job Description And Salary Fieldengineer

5 Must Implement Cyber Security Strategies For 19 Coffee With Cis Latest News Articles

Its It Security Pace University

It Security What Is It Techradar

How To Start Your Cyber Security Career Connected It Blog

What Are The Different Types Of It Security Rsi Security

Taking Responsibility For Cyber Security In A Truly Virtual World

Creating A Covid 19 Cyber Security Plan Connected It Blog

Cybersecurity Vs Information Security Is There A Difference Cloud Academy

Methods For Easing Your Top Cyber Security Challenges Channel Futures

It Security Coordinator Sign Up To Freelance

Information Security Cybersecurity It Security Computer Security What S The Difference Hacker Noon

How To Practice Cybersecurity And Why It S Different From It Security Cso Online

Few Execs Believe Healthcare It Security Tech Will Be Disruptive

3 Essential Components Of Your It Security Roadmap

It Security Connection Public Sector Solutions
What Is State Of The Art In It Security Enisa

What Is It Security Information Technology Security Cisco

Why Is Cyber Security Important It Company Birmingham

What Is An It Security Audit
It Security Party Tricks Cybersecurity Insiders

Is A Cyber Security Degree Worth It The Facts You Can T Ignore Rasmussen College

International Law On Cyber Security In The Age Of Digital Sovereignty

The Top Ai Cyber Security Companies Information Age

Cyber Security Strategy Solutions Conet De

It Security Roles And Responsibilities Simplilearn

12 Top Tips For Cyber Security Context Information Security

12 Things Every It Security Professional Should Know Cso Online

Cyber Security Monitoring Network Monitoring Redscan

Cyber Security Insurance On The Rise Aws Insurance Company

Information Security Training For Staff Why You Need It How To Do It

4 It Security Best Practices Smbs Need To Adopt Immediately Bytestart

10 Cyber Security Tips Fro Small Business Pentucket Bank

It Security Vs Cybersecurity Cybersecurity Comptia

Industrial Cyber Security Why It Ot Collaboration Is No Longer An Option But A Necessity

What Is Cyber Security Definition Types And User Protection Kaspersky

No Shortcuts To Effective Cyber Security Amp Information Systems

Bank It Security Can Still Learn From 15 Top Takeaways Part 1 Thales Blog

Top Jobs In It Security It Security Job Designations Simpilearn

The Future Of Network Security Is Now Whether We Like It Or Not 05 14 Security Magazine

The Rising Costs Of Cybersecurity Breaches Why It Security Is Doomed To Fail

The Human Factor In It Security How Employees Are Making Businesses Vulnerable From Within Kaspersky Official Blog
1

How To Better Integrate It Security And It Strategy Cio

What Is An It Security Audit The Basics Varonis

It Security Compliance Solutions Itelligence North America

Cto Vs Ciso Who Should Have Ultimate Responsibility For Cyber Security

Opinion Cyber Security A Complex Behaviour Problem

The Role Of An It Security Professional Technojobs Uk

It Security Nasa

Cyber Security A Necessary Component Of Railways In The Digital Age

It Security Vs Cyber Security What Is The Difference Logsign

Telekom Delivers It Security Deutsche Telekom

Ethical Issues Behind Cybersecurity Maryville Online
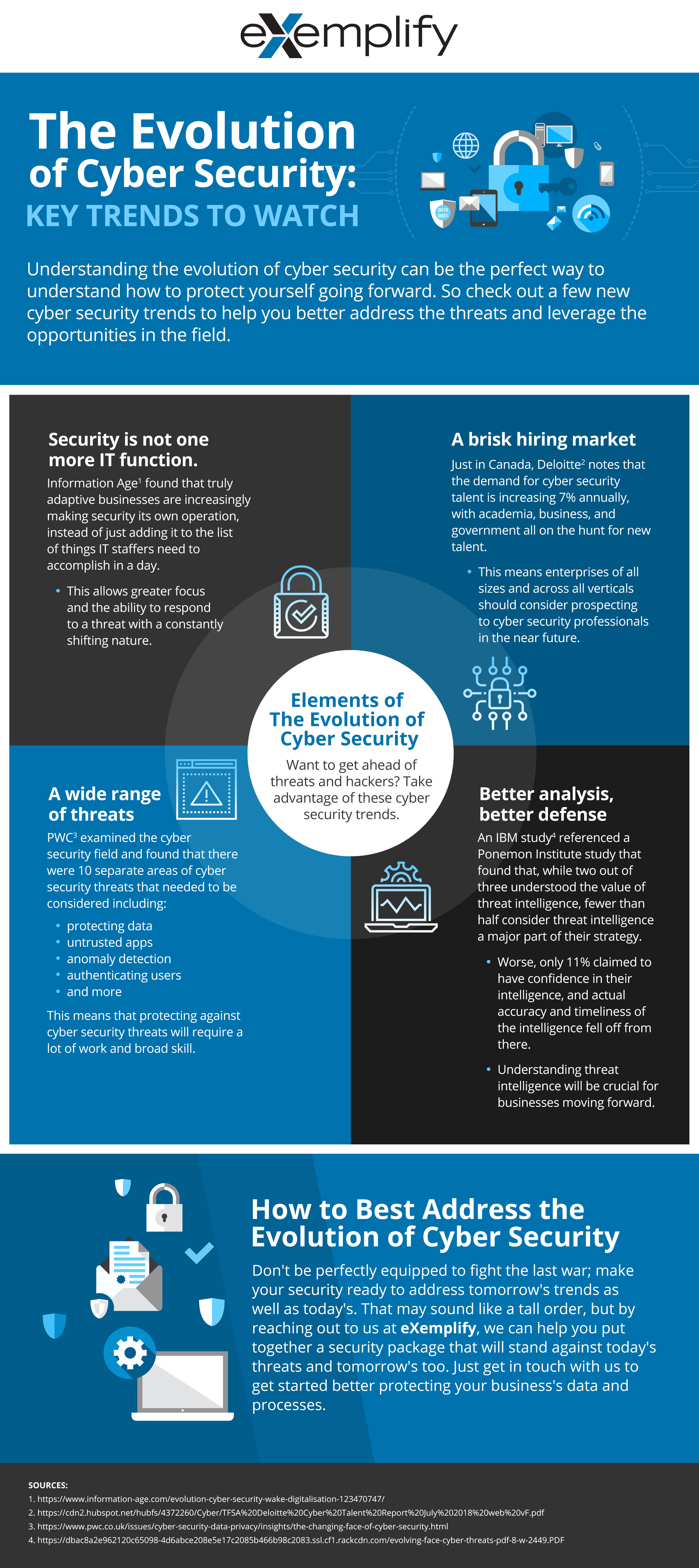
Infographic The Evolution Of Cyber Security Key Trends To Watch Exemplify More Than A Master Agent

It Compliance Vs It Security What S The Difference Bmc Blogs

It Security Law Enforcement Cyber Center

What Are The Types Of Information Security Controls Reciprocity

How Much Does A Cyber Security Specialist Make
Q Tbn 3aand9gcts9vp7bzr Jhsa5gygmkud987udyghypriulccreuznsghb Qc Usqp Cau

Cyber Security Dtu

It Security Risk Assessment Methodology Securityscorecard

What Is Cyber Security A Beginner S Guide Rasmussen College
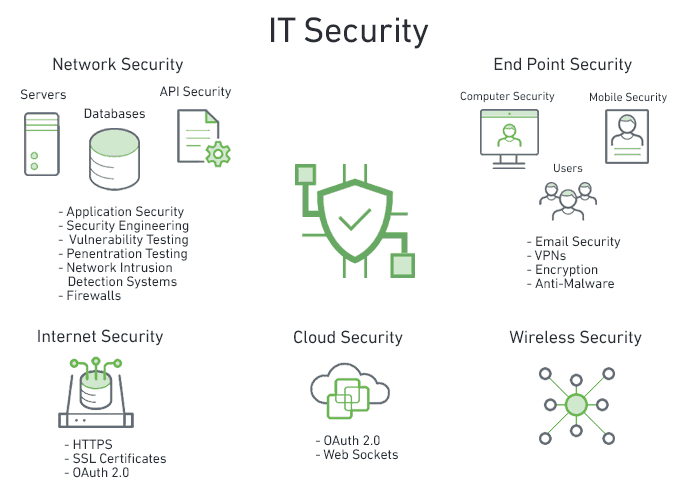
It Security What You Should Know

10 Common It Security Risks In The Workplace
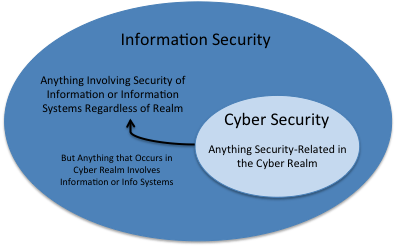
What Are The Different Types Of It Security Rsi Security

Cybersecurity Awareness Is About Both Knowing And Doing

Critical Information Systems And Cybersecurity Thales Group

Security For Safety S4s

Cyber Security Vs Information Security Is There A Difference Gw Cybersecurity Online

10 Signs You Should Invest In It Security Excalibur Communications
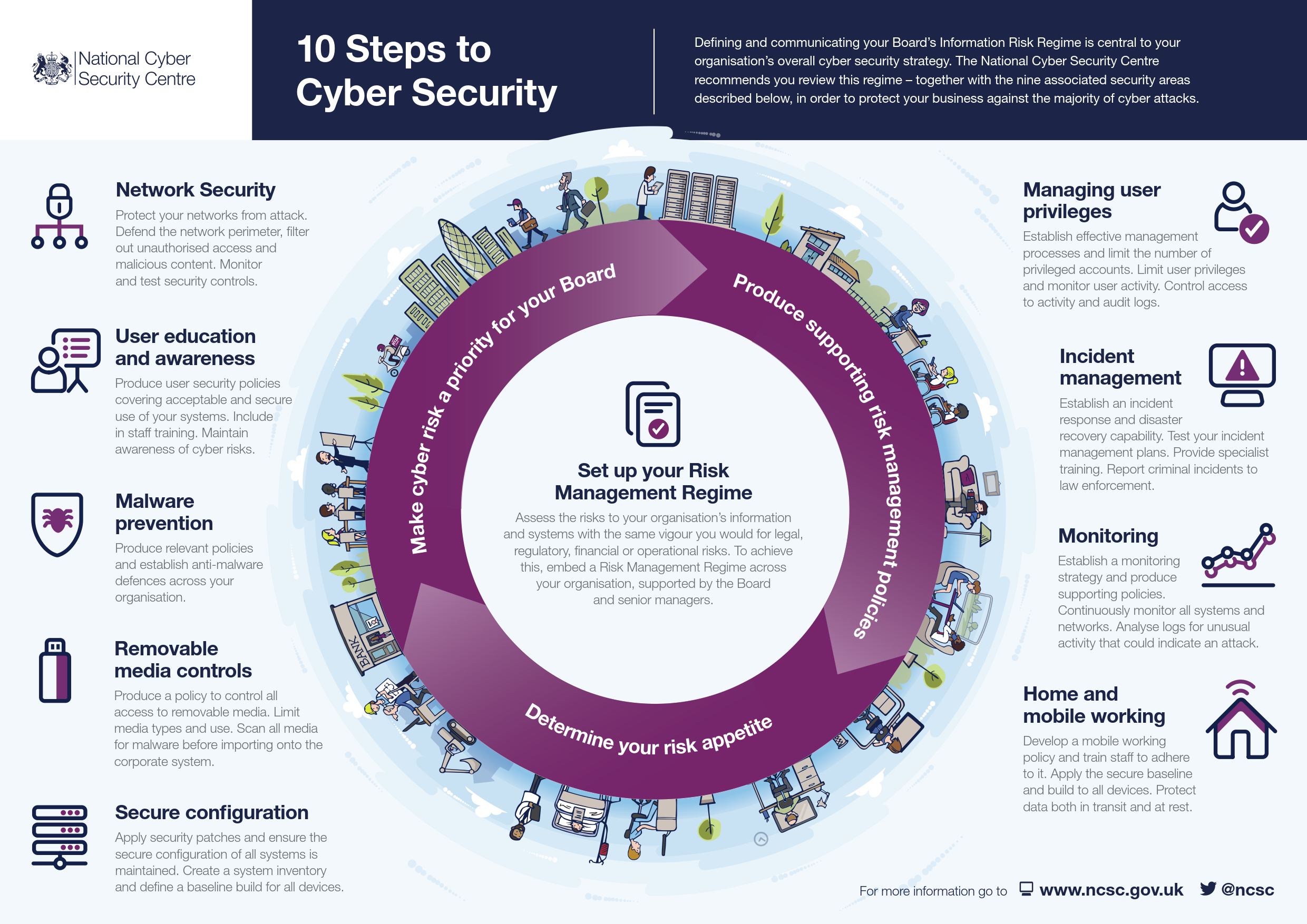
Infographic Ten Steps To Cyber Security Safety4sea

It Security Policy Template Free Privacy Policy

What Is An It Security Audit Cheeky Munkey

4 Easy Steps How To Conduct It Security Audit Of Your Own Company

How To Protect Your Practice From Cyber Attacks With Cyber Security

It Security Services Information Security Management Service Infopulse

Why It Security Will Be A Prime Concern For Businesses In The Next Decade

Why Multiple Layers Of Cyber Security Is Essential Lms Group
Top 10 Cyber Security Threats For 17 Shred It United States

Why Is Cyber Security Important In 19 Securityfirstcorp Com

Healthcare It Security Worst Of Any Sector With External Threats
Q Tbn 3aand9gctjedxcyvmgs Kb5vm Erzwlnlptlu1lczy33c1cpaanrqdfcga Usqp Cau

Why Segregation Of Duties Is Crucial For It Security Network Security

Top 10 It Security Stories Of 18

23 Top Cyber Security Certifications For It Business Professionals

It Security Policy Development Infosight

Shouldering Responsibility For It Security A Multi Stakeholder Approach Self Regulation In Practice For A Better Internet Issues Dotmagazine

Managed Security Services Irvine Ca Cybersecurity Vology
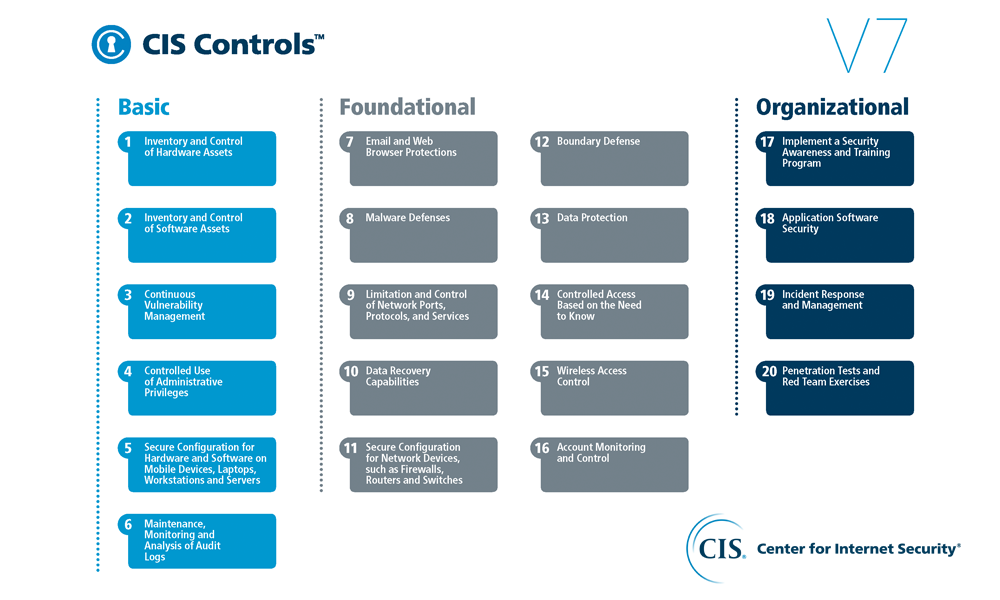
It Cyber Security Discovery Lansweeper It Discovery Software

It Security Threats Are Taking More Time To Remedy Than Ever Itproportal

It S Time To Distinguish Information Security From It Security Nucleus Cyber




